India will be the largest victim of broadcast piracy in the world by 2022: Sandeep Singh
In an indepth interaction with Adgully, Sandeep Singh, Product Marketing Manager, Media and Entertainment, Akamai Technologies, speaks at length about content theft and piracy in India, the cost to the media and entertainment industry, how to counter piracy and much more.
What are the revenue losses and lost monetisation opportunities for the M&E industry in India due to content theft and piracy on an annual basis? What kind of YoY escalation is this menace seeing?
The cost of global online streaming piracy will hit $52 billion by the year 2022, according to a report by Digital TV Research. Nearly 190 billion visits were made to illegal piracy websites in 2018, 17.4 Billion from the US, followed by Russian Federation (14.5 Billion), Brazil (10.3 Billion), India (9.6 Billion) and UK (5.75 Billion) as the other top nations affected by online piracy. In terms of the type of content pirated, almost 50% of visits to the pirated websites were for television shows, and nearly 20% of visitors were looking for the latest released movie.
The Online TV and movie revenue lost to piracy in India is expected to reach $3.08 billion by 2022. The advent of live streaming apps has also led to rampant piracy of sports broadcasts worldwide, including India. While there are no recent statistics quantifying the losses to the Indian broadcasting industry due to sports broadcast piracy, the overall losses because of online piracy is estimated to touch up to $3.1 billion by 2022, making India the largest victim of broadcast piracy in the world.
How does the content piracy ecosystem operate?
Security in the media & entertainment industry means securing the entire content delivery path. Any media company that wants to serve or distribute its content to end users, needs to protect itself from attacks that can originate at multiple points across the content delivery path.
For example, the content might be at risk when it is created within the content production workflow or during post-production or even when 3rd party players try to access the content production system, for example, translation companies. The content might be at risk during the workflow stages, when it moves through the content workflow where it gets converted into different formats for different devices and is stored for distribution. Finally, the content can also be at risk when it is decrypted and distributed to the end users via different channels.
The risk to the content mainly happens from “Bad Actors” or pirates who want to get unauthorised access to content for multiple reasons. It could be illegal subscriptions or credentials to gain illegit access to content or service disruptions to cause reputational damage through Denial of service (DDoS) or it could be hackers trying to get access to the raw content asset to manipulate it and distribute via torrent sites or other pirated websites.
So, while organisations need enterprise and infrastructure security solutions to safeguard themselves at the production and distribution stages, they also need specific security solutions to safeguard themselves against online piracy and threats to the content assets itself.
You can shut down one source of piracy, but other sources crop up elsewhere. Is it possible to provide content protection on a real-time basis and how?
Video content consumption is becoming mainstream in India, fueled by the widespread availability of content, hyper-connected devices and ubiquitous high-speed data. This is making piracy a real and present-day danger for media organisations. There are new and evolving threat vectors, including credential sharing to re-distribute content from unauthorised sources, use of sophisticated piracy tools like re-encoders or stream ripping tools to grab the content and redistribute it as well as circumvention of geo-restriction by use of Virtual Private Networks (VPNs) and proxy servers. All these threat vectors keep changing as pirates keep becoming smarter and hence the ability to detect a threat in real time and taking necessary remediation action becomes necessary.
Akamai’s Access Revocation solution provides media organisations the ability to revoke an active video streaming session in real-time that is either unauthorised or is the source of piracy. The Access Revocation API provides customers the ability to revoke or authorise at subscriber, content & playback session levels, works for both Live streaming and On-Demand streaming use cases and has a near real time latency for the token identifier called via the API to revoke access.
What is the most frequent kind of security breaches seen?
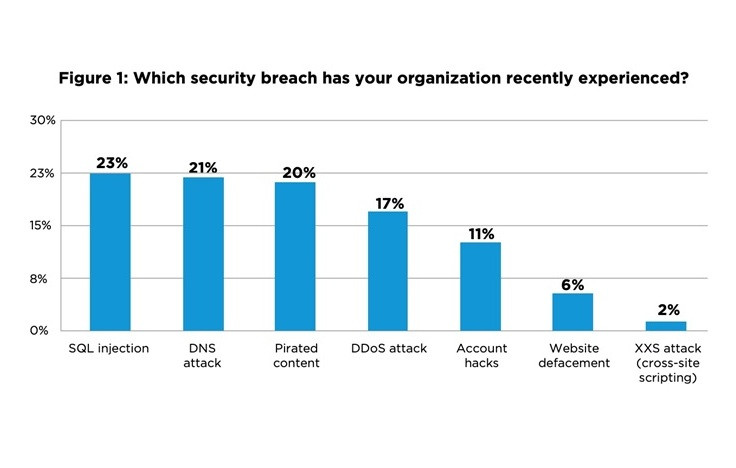
According to a survey of almost 200 media technology influencers and decision-makers conducted by Akamai in 2018, attacks on media organisations are widespread and of different types. The four most frequent breaches according to the survey were:
- SQL injections (23%)
- DNS attacks (21%)
- Content pirating (20%)
- DDoS (17%)
One of the emerging areas of threat for media and entertainment organisations is “Account Hacks”, which, according to the survey, stood at 11%. As OTT companies are increasingly focusing on Subscription based models, ensuring safety of subscriber data is also becoming critical.
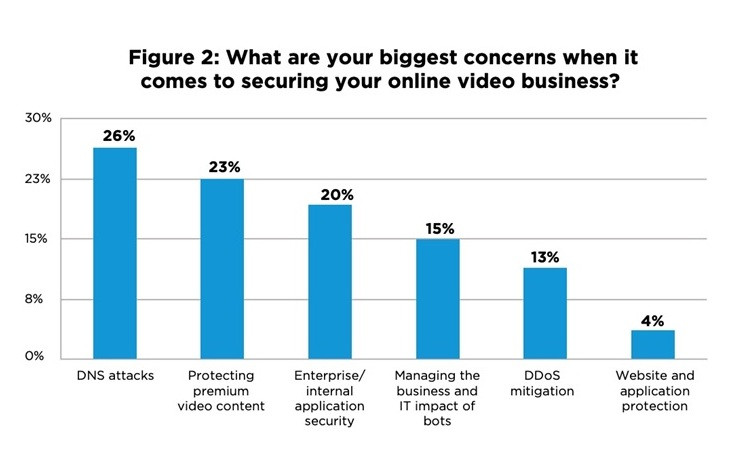
In terms of the biggest concerns to secure online video businesses, the survey revealed that though service downtime, caused by DNS based attacks or DDoS attacks are important, the second highest area of concern was protecting premium video content (23%).
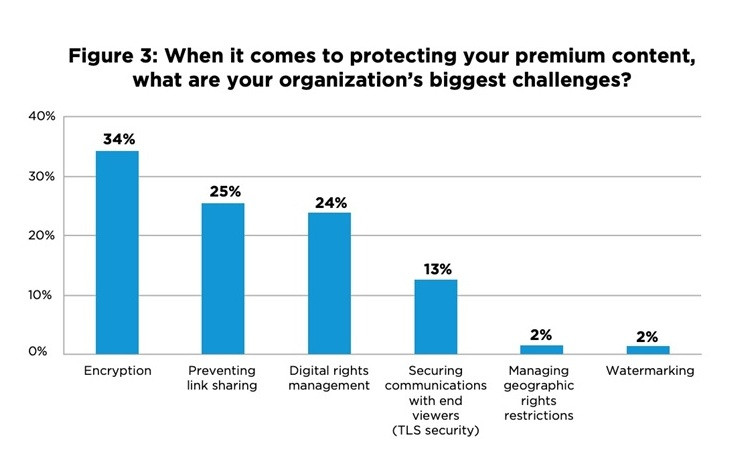
Premium Content is key to a Successful Video Strategy, or in other words, content is the king, but it must be protected. For M&E organisations to monetise premium video content, they need to protect the content against unauthorised usage and distribution. Based on the survey, organisations face a few challenges in implementing technologies to prevent content piracy.
The Akamai content protection portfolio is designed in a way to help media organisations defend themselves against these critical threat vectors so that these organisations can focus on their core, that is creating and distributing content and offload the threats related to safeguarding it.
How is Akamai helping organisations protect themselves against content theft and piracy?
Akamai provides a robust content protection solution portfolio to help media organisations prevent piracy and unauthorised access, while maximising the monetisation opportunities for premium content. The portfolio is segmented into three key capabilities:
Preventing Theft: Capabilities designed to prevent theft of the content asset to Link Sharing & Content Piracy. There are three solutions under this capability:
- Token Authentication: Authenticates users using tokens and session level parameters to prevent unauthorised sharing of links. Also supports browsers and platforms that don’t use cookies.
- Access Revocation: Provides an additional layer of protection by providing the ability to revoke an active video streaming session in real time that is either unauthorised or is the source of piracy.
- Media Encryption: Protects HLS video content against unauthorised viewing by applying scalable session level AES128 encryption at the edge.
Protect Access: Capabilities to protect unauthorised content access from unauthorised users, locations, and devices. There are three solutions under this capability:
- Watermarking: A two-step watermarking solution that provides an edge function to do AB switching on the edge that is robust, secure, scalable, and works with leading watermarking solutions.
- Enhanced Proxy Detection: Bolster protection against geolocation fraud and piracy. Intelligently block requests associated with an anonymous proxy or VPN service using afully integrated VPN and DNS Proxy detection service.
- Content Targeting: Enhance compliance with content rights restrictions by using geo-blocking, which restricts user requests to access content from outside a defined geographic location.
Secure Communication: Capabilities to secure communications with users over HTTPS, using TLS. There are two solutions under this capability:
- Standard TLS: A secure delivery feature that encrypts data in transit using TLS to prevent hijacking or snooping. It supports custom domains and provides performance at scale by delivering HTTPS traffic with similar offload, throughput, and latency as HTTP traffic.
- Enhanced TLS: A secure media delivery option that provides HTTPS delivery using a custom certificate with added security measures, including physical security guarantees for customers that need to maintain PCI compliance.
Could you tell us about Akamai’s watermarking technology and how it is helping content publishers and platforms tackle the problem of piracy?
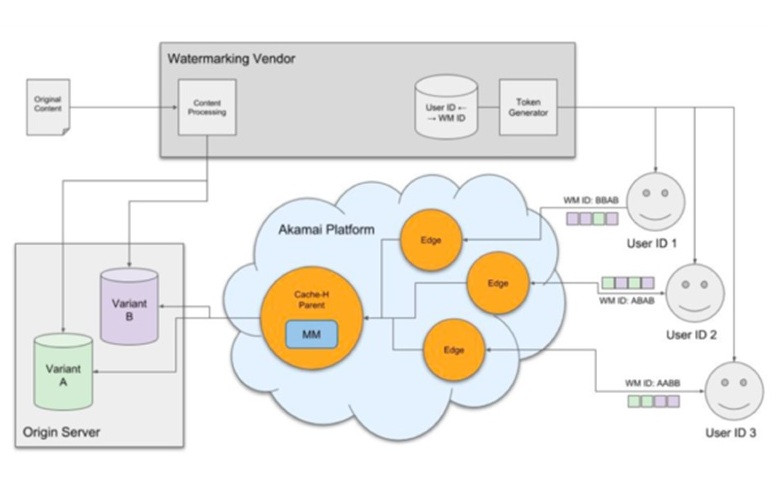
Akamai's edge-based Watermarking solution is a 2-Step watermarking solution that provides an edge function to do AB switching on the edge that is robust, secure, scalable and works with leading watermarking solutions.
Post-decryption theft is one of the major weak links in the content distribution value chain. We commonly come across scenarios where illegal devices are used to record and distribute content, for example, content being stolen which being streamed online or mobile devices being used to record movies at theatres etc. For scenarios like these, using Watermarking to prevent content from being pirated by marking the content to determine the source of the content leak becomes important.
Watermarking can be used for various use cases within the M&E industry, like protecting copyright information, monitoring premium content, preventing unauthorised content copying and content tampering. By dynamically adding unique, imperceptible watermarking within the video that identifies the source or intended recipient of the content, each genuine copy of the content can be differentiated from the pirated content to trace piracy leaks back to the source and take anti-piracy actions.
Akamai’s Watermarking solution is currently pre-integrated with technology from Nagra, Verimatrix, Irdeto and ContentArmor, four of the leading providers of watermarking services, with more partners to follow soon. The solution is easy to integrate with and supports integration with “Do-It-Yourself” or other 3rd party watermarking solutions using Akamai integration specs.
With subscriber data security becoming an important concern for media and entertainment companies, how can Akamai help companies tackle this problem?
Keeping customer data secure and protected from malicious actors is as important as privacy. As identity data can easily be abused and exploited, it has become a major target for hacking attacks. The 2018 Cost of a Data Breach Study, conducted by IBM Security and Ponemon Institute, found that almost half of the organisations represented in that research (48%) identified the root cause of a data breach as a malicious or criminal attack, with an average cost of approximately $157 per breached identity record. As breaches frequently involve hundreds of thousands (or even millions) of records, the resulting cost can severely harm a company – and that’s before the revenue loss associated with reputational damage and loss in customer trust is calculated.
Akamai’s Identity Cloud solution helps media and entertainment organisations protect and secure end user data and credentials with strong encryption and scoped access control. The solution facilitates compliance with regional privacy regulations around the world and delivers end user data privacy. It is also designed to allow companies to offload and simplify identity architecture and data, while delivering high reliability, global scalability, and low-friction customer experiences. Identity Cloud [has the broadest set of independent security certifications in the industry] to ensure that the Personally Identifiable Information (PII) data that customers provide when registering their accounts is safeguarded.
Accounts are protected against abuse with strong user authentication methods, including federated login, traditional login, two-factor, single sign-on (SSO), social login and one-time-password (OTP) authentication.
Also Read:
Google Home and Amazon Echo spy on you, ALL THE TIME!
Amid growing security concerns, social media majors take a stand to make platforms safer

















Share
Facebook
YouTube
Tweet
Twitter
LinkedIn